6 Reasons Not to Pay the Ransom in a Ransomware Attack
One of the greatest threats facing businesses today is the risk of a ransomware attack. By encrypting data, hackers effectively lock companies out of their computer systems, bringing operations to a halt and in some [...]
Implementing Automated Incident Response in Your Business
If a data breach occurs, your business needs an incident response plan to act quickly and prevent as much damage as possible. As the rate of cyberattacks increases worldwide, automated incident response programs have made [...]
This is Not Business as Usual: Strategies for a Strong Defense
“We know that our neighbors and partners across the world are also under attack. This is not innocent. This is not business as usual. Just look at these attacks. Look at how pervasively they are [...]
Update on Cybersecurity Standards – 2023: Most Widely-used Standards & Frameworks
An important aspect of a proactive and effective cybersecurity initiative is the inclusion of content and guidance from the many available domestic and international standards and guidance documents. This article lists the most important and [...]
How to Declutter Your Current Cybersecurity Operations
With 2.8 billion attacks recorded globally, the first half of 2022 saw an 11% increase in cyberattacks over the entire year of 2021. On the part of organizations, this betrays a lack of adaptation to [...]
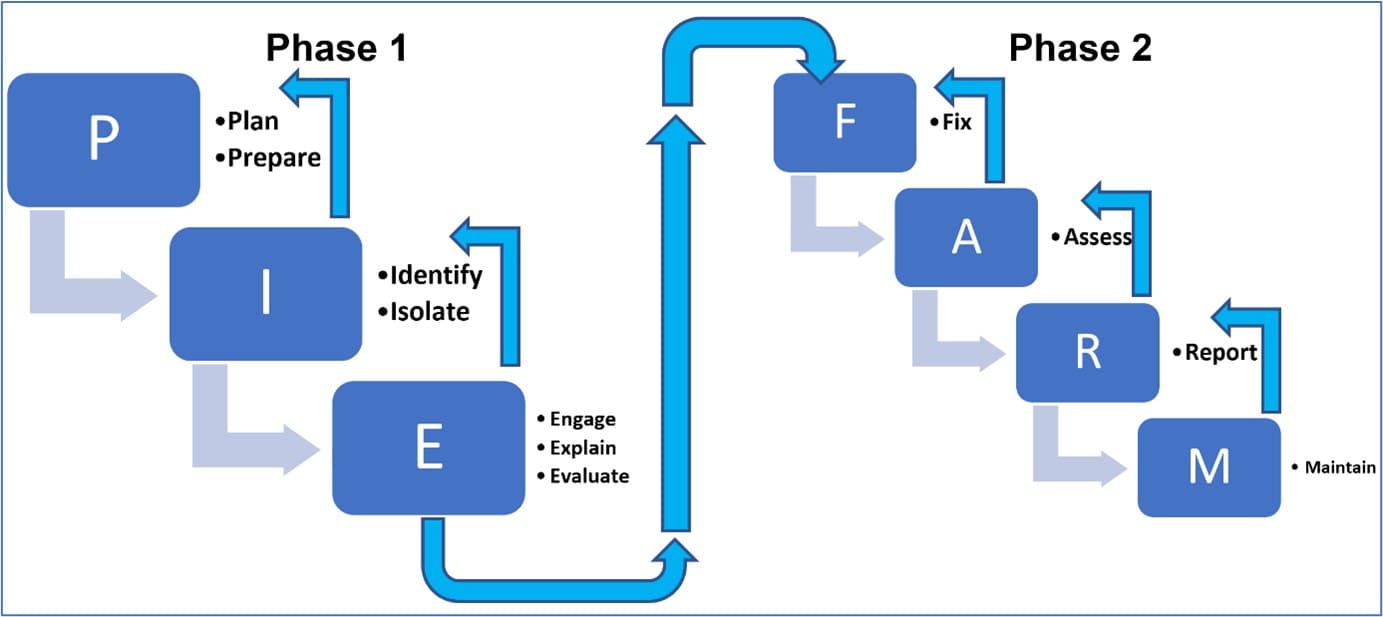
Enhancing Digital Operational Resilience: The PIE FARM Approach
In today's interconnected and technology-driven world, businesses are increasingly reliant on digital systems to operate efficiently. However, with technological advancements come vulnerabilities that can disrupt operations. To mitigate these risks, organizations must develop robust Digital Operational [...]
Data Loss Statistics that Prove Every Business Needs a Backup Solution
The modern world runs on data, and without it, things quickly grind to a halt. Businesses use data for everything, including sales, marketing, logistics, and staffing. What happens when that data is lost? Taking a [...]
Good and Bad Advice on Cybersecurity Audits
Is cyber really a top-ten risk? In order to know, each organization needs to conduct and continuously (or close to it) update its cyber risk assessment – within the context of the enterprise risk management [...]
What Does Good Look Like, for Information Technology and Cyber?
Eliminate outages, failures, and downtime, ensure that there are “no single points of failure”. How easy would it be to achieve this? I was recently in a conversation with a Chief Information Security Officer (CISO) [...]
Why Cybersecurity and Physical Security Need to Work Together
Let’s say the access control system at your organization was hacked, and someone without authorization was able to enter a secure area. Is that a cyber attack, or is it a physical one? It’s obviously [...]
The 7 Deadly Cyber Sins We All Should Avoid
Cyber thieves are on the prowl. Each day, we work with decision makers on a variety of security and resiliency issues. While they remain worried about building fires, COVID-19, and hurricanes, they don’t quite realize [...]
Be Like Netflix, not Reddit: SaaS Disaster Response
I don’t know how people got anywhere without Google Maps. I hear they printed out a “Map Quest,” whatever that is. As a kid, I assumed that adults just knew all the direction and that [...]